On February 10th 2015, Microsoft published Security Bulletin MS15-011, which detailed a recently discovered critical flaw in every major version of Windows from Server 2003 right the way through to Windows 8.1. The flaw, relating to how Group Policy handles data, potentially allows:
…remote code execution if an attacker convinces a user with a domain-configured system to connect to an attacker-controlled network. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
Microsoft was quick to release a corresponding security patch via the Windows Update service and each corresponding Operating System update can be downloaded and installed via the links below
- MS15-011: Windows Vista Service Pack 2
- MS15-011: Windows Vista x64 Edition Service Pack 2
- MS15-011: Windows Server 2008 for 32-bit Systems Service Pack 2
- MS15-011: Windows Server 2008 for x64-based Systems Service Pack 2
- MS15-011: Windows Server 2008 for Itanium-based Systems Service Pack 2
- MS15-011: Windows 7 for 32-bit Systems Service Pack 1
- MS15-011: Windows 7 for x64-based Systems Service Pack 1
- MS15-011: Windows Server 2008 R2 for x64-based Systems Service Pack 1
- MS15-011: Windows Server 2008 R2 for Itanium-based Systems Service Pack 1
- MS15-011: Windows 8 for 32-bit Systems
- MS15-011: Windows 8 for x64-based Systems
- MS15-011: Windows 8.1 for 32-bit Systems
- MS15-011: Windows 8.1 for x64-based Systems
- MS15-011: Windows Server 2012
- MS15-011: Windows Server 2012 R2
- MS15-011: Windows Server 2008 for 32-bit Systems Service Pack 2
- MS15-011: Windows Server 2008 for x64-based Systems Service Pack 2
- MS15-011: Windows Server 2008 R2 for x64-based Systems Service Pack 1
- MS15-011: Windows Server 2012
- MS15-011: Windows Server 2012 R2
Now, you may be asking at this point, why are you posting about this now in mid-2018? Surely the vulnerability has been addressed on all affected systems that are patched regularly? Well, as I found out very recently, this security patch is one of many released by Microsoft that requires additional administrator intervention after installation to ensure that the exploit hole is properly filled. The modifications required can be completed either via the Local Group Policy Editor for single machines not joined to a domain or Group Policy Management Console from a domain controller. The second option is naturally preferred if you are managing a large estate of Windows machines. Below are summarised steps that should provide the appropriate guidance on applying the fix for both environments
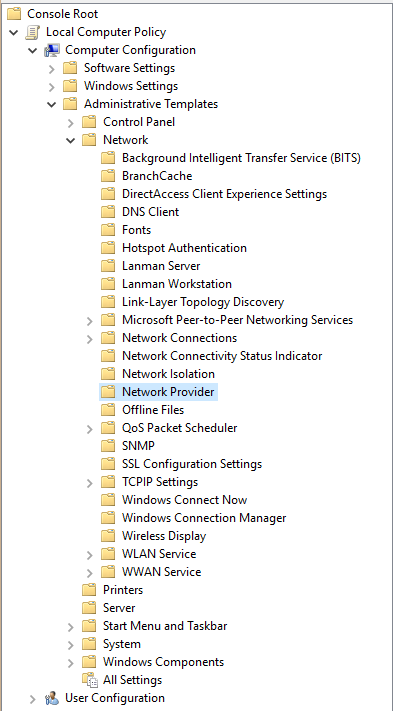
- Navigate to the Management Editor and expand and open up the Computer Configuration/Policies/Administrative Templates/Network/Network Provider folder path.
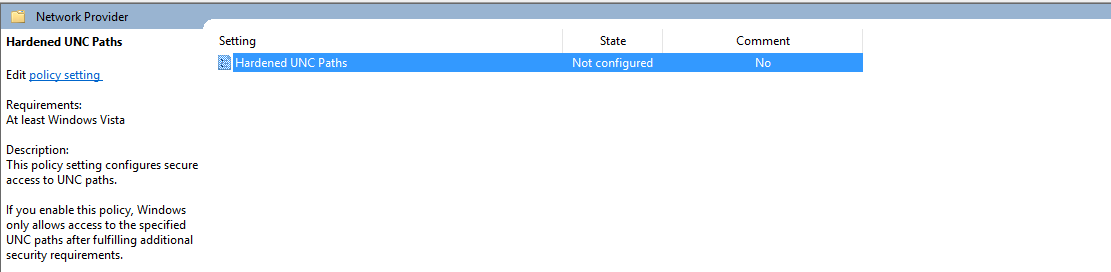
- On the right-hand pane, you should see an item called Hardened UNC Paths, marked in a state of Not configured. Click on it to open its properties
- There are then a couple of steps that need to be completed on the pop-up window that appears:
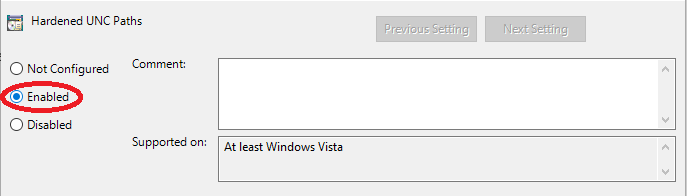
- Ensure that the Enabled box is selected.
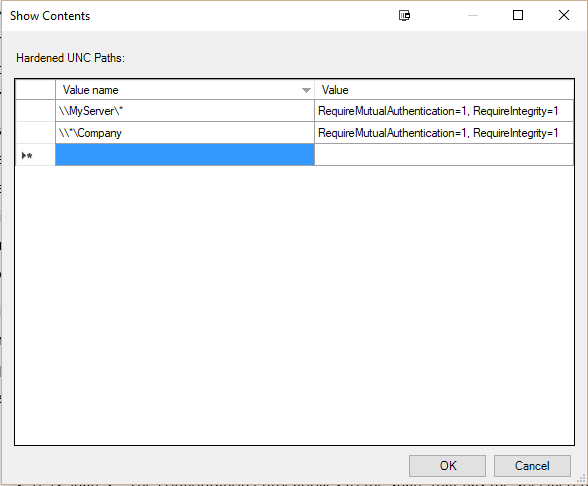
- In the Options tab, scroll down to the Show… button and press it. The options at this stage depend upon your specific environment. For example, let’s assume that you have a domain with a file server called MyServer, which is configured for shared access. The most appropriate option, in this case, would be a Value name of \\MyServer\* with a Value of RequireMutualAuthentication=1, RequireIntegrity=1. Another example scenario could be that multiple Servers are used for sharing out access out to a share called Company. In this case, you could use the Value name option of \\*\Company with a Value of RequireMutualAuthentication=1, RequireIntegrity=1. Both of these examples are reproduced in the screenshot below, for your reference. Press the OK button to confirm the UNC path fields and Apply to make the policy change.
- The final step will be to enforce a group policy refresh on the target machine and any others on the domain. This can be done by executing the gpupdate /force Command Prompt cmdlet and confirming that no errors are generated in the output.
And that’s it! Your Windows domain/computer should now be properly hardened against the vulnerability 🙂
This whole example represents an excellent case study on the importance of regularly reviewing security bulletins or announcements from Microsoft. The process of carrying out Windows updates can often become one of those thankless tasks that can grind the gears of even the most ardent server administrators. With this in mind, it can be expected that a degree of apathy or lack of awareness regarding the context for certain updates can creep in, leading to situations where issues like this only get flagged up during a security audit or similar. I would strongly urge anyone who is still running one or all of the above Operating Systems to check their group policy configuration as soon as possible to verify that the required changes indicated in this post have been applied.